More and more organizations are modernizing their IT infrastructures to adopt “zero trust” architecture, even the White House Executive Order 14028, “Improving the Nation’s Cybersecurity” is giving government agencies a significant push towards zero trust. It is critical for anyone who’s planning such a transition to understand how to build a strong foundation.
“Trust no one. Suspect Everyone.”
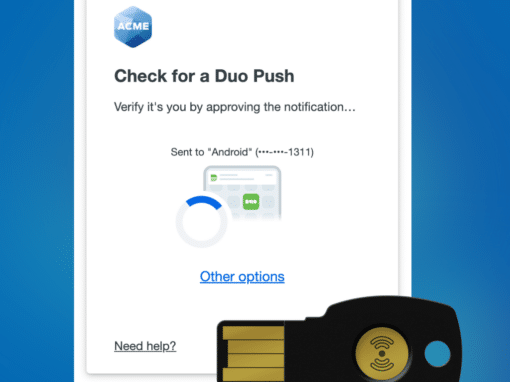
Zero trust is an architectural shift from the traditional perimeter network security model to the new identity-based model. Instead of establishing trust based on an endpoint/user’s network perimeters, zero trust depends on the actual identities. This means, instead of assuming trust based on a device or user’s network attributes (IP range, network subnet mask, geolocation, etc.), zero trust starts with the user/device’s authentication result, and only provision appropriate trust assigned to the user/device. Therefore, it is crucial to have a proper multi-factor authentication solution to build a solid zero trust architecture.
It is also noteworthy to point out that not all MFAs are created equal. We strongly advise against using SMS-based MFA as it is susceptible to be attacked via various techniques such as SIM-cloning, social engineering, and other weaknesses in the SMS/telephone network layers. Just look at the recent events around Coinbase and Telegram.
To recap, build your zero-trust infrastructure with the proper foundation- starting with a strong form of multi-factor authentication using hardware security keys. FEITIAN Technologies can help you and your organization to implement the appropriate base layer, the building blocks to your security infrastructure.
FEITIAN has a comprehensive portfolio of certified security keys: OATH OTP tokens and cards, FIDO U2F keys (optionally with PIV and smart card feature enabled), FIDO2 keys, and state of the art, FIPS-140-2 certified FIDO2 biometric keys. Learn more.


Enrique Tang is a passionate technologist who recently joined FEITIAN as a Head of Technical Solutions Sales. He came from Google with 14 years of experience in IT systems, solutions engineering, and program management. In his leisure time, he can be found dabbling into various arts on his website at heta.link.
View profile