




Solutions for Cyber Threats
Cyber Threat Details




featured solutions
Account Takeover
Phishing
Cyber Attacks
Physical Security
Payment Fraud
Case Studies & White Papers

Authentication, White Paper
Best Practices for Seamless FIDO Implementation
A complete overview of the FIDO authentication framework, its key principles, and the benefits it offers for enhancing security and user experience.

Authentication, Solution Note
Healthcare institutions are held to high standards in the U.S. through HIPPA, HITRUST, and FIPS for securing systems, data, transactions, communication, access, authentication, and more.

Authentication, Company News
Introducing FKaaS: FEITIAN Keys as a Service
With FKaaS, enterprises can now access FEITIAN's FIDO Certified phishing-resistant multi-factor authentication (MFA) security in a more flexible and scalable manner.

Authentication, Solution Note
Duo + FEITIAN = Phishing Resistant FIDO2 MFA
Cisco Duo helps companies protect their data at scale with zero trust security platform – pair it with FIDO Certified keys from FEITIAN for phishing-resistant MFA.

Authentication, Solution Note
Revolutionizing Banking Security with FIDO
Passwords, OTPs, and 2FA are no longer enough to negate cyber criminals, especially for sensitive environments like banking and finance institutions.
Authentication, Case Study
Empowering Government Agencies With PIV & CAC Sign-
A groundbreaking solution developed by our longstanding technology partner, Twocanoes, offers a game-changing approach to PIV and CAC card authentication on iOS devices.
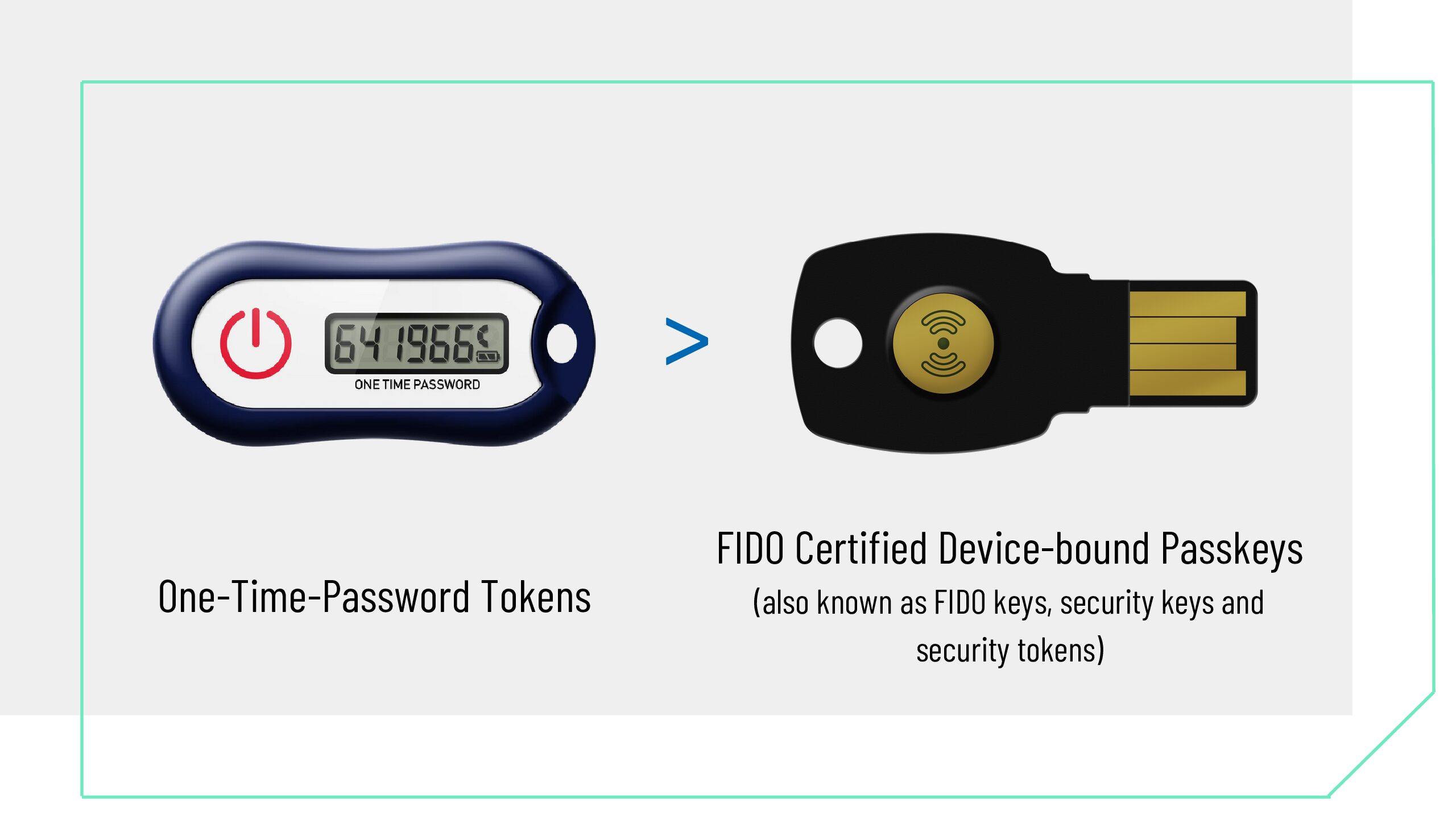
Authentication, Solution Note
OTP to FIDO Transition Solution Note
Download our Solution Note to discover how FEITIAN can help upgrade your authentication security from legacy OTP, to FIDO security Keys.
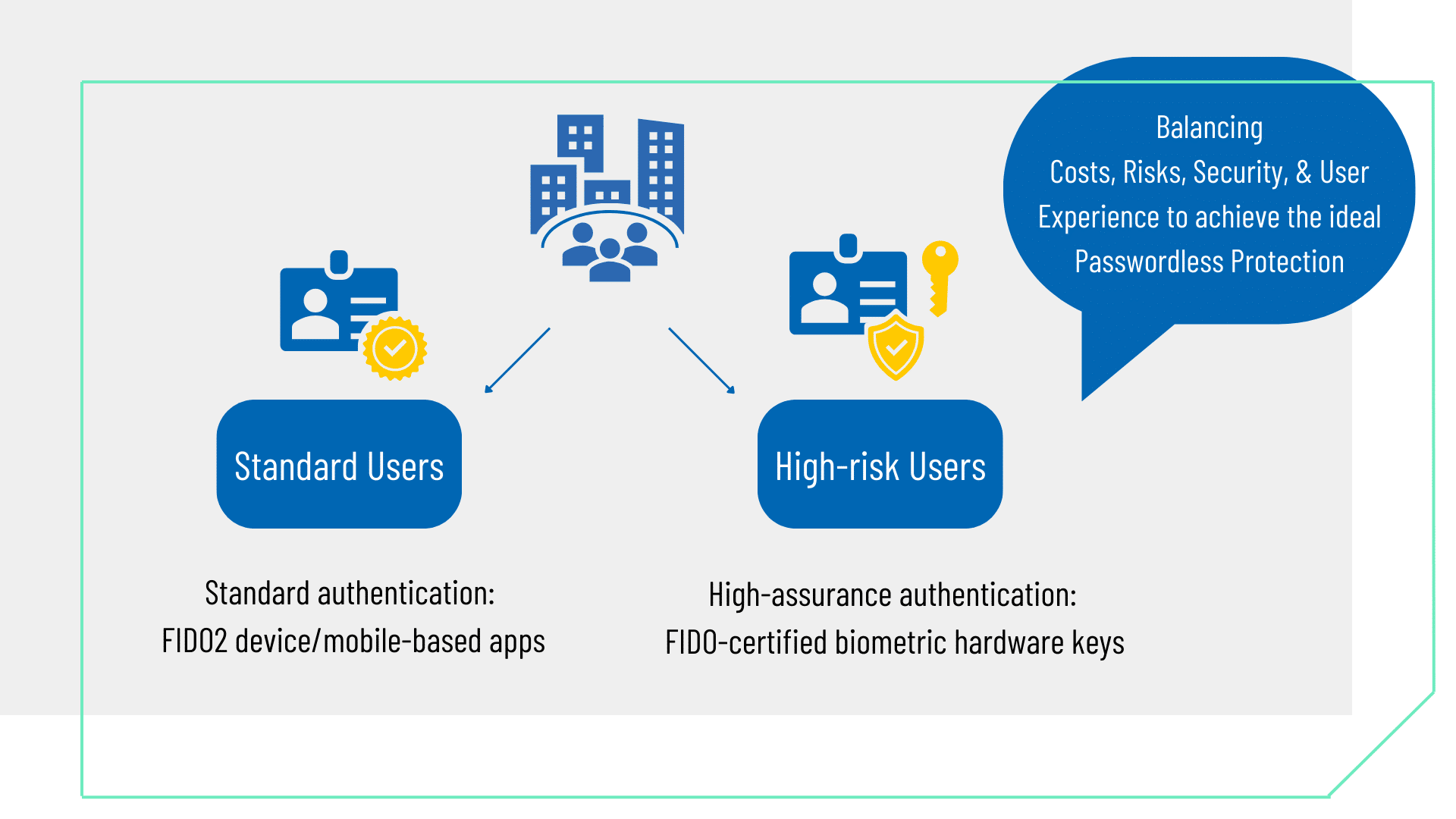
Authentication, Case Study
Case Study: Enterprise
This case study profiles one of our longstanding enterprise customers who selected and deployed FEITIAN FIDO2 security keys as part of their passwordless journey.

Authentication, Solution Note
Microsoft Entra ID Solution Note
Download our solution note to discover how FEITIAN and Microsoft Entra ID can safeguard your digital assets today.

Authentication, Solution Note
FIPS + FIDO Solution Note
True Passwordless Protection from FEITIAN with FIPS + FIDO Certified Keys.

Authentication, White Paper
Everything You Need to Know About Fido
A comprehensive overview of the FIDO (Fast Identity Online) authentication framework, it's key principles, implementation, and the benefits it offers for enhancing security and user experience.
Authentication, Solution Note
What Role Does Multi-Factor Authentication Play in Cyber Security
In today's digital age, cyber threats are on the rise, and it is more important than ever to secure every endpoint and data. With the increasing frequency and sophistication of cyber-attacks, traditional authentication methods like usernames and passwords are no longer enough.
Authentication, Solution Note
Different Types of MFA & What You Need to Know
Multi-factor authentication (MFA) is a vital component of digital security, neutralizing the risks associated with compromised passwords. Different types of MFA, such as phone callbacks, SMS-based OTP, OTP tokens, and mobile authenticator apps, offer varying levels of security and convenience.
Coming Soon…
Looking for a specific resource? Let us know!
SIGN UP TO DOWNLOAD
Already submitted? Check your email for the download link.
Certifications






Relevant Posts
3 Ways to Meet Upcoming CJIS Authentication Mandates

Outsmarting Attackers by Deploying FIDO2 in Education

FEITIAN’s Secure your Summer FIDO Sale
Questions? Get In Touch With Our Support Team
We understand the importance of timely and reliable support when it comes to your security solutions. By filling out our contact support form, you can reach out to our experts who will provide prompt and personalized assistance to address your specific needs


