Are authenticator apps accessing data on your phone?
Why should I use an authenticator app?
Why is an authenticator app safer than an SMS text message?
How to set up an authenticator app with your online accounts
Gartner, the leading provider of IT market research and consulting services has reported 88% of executives now consider cybersecurity as a direct threat to an organization’s operations rather than solely and isolated IT concern. An organization’s identity systems and misuse of credentials has been identified as a hacker’s primary gateway to an organization’s sensitive information. These security risks are sharply mitigated, and identity access management (IAM) goals achieved with the deployment of an authenticator app which:
- Is an effective solution for organizations seeking cloud-based, scalable user and network protection without complex software configurations, needing to manage security appliances, or expensive support contracts.
- Provides a simple to use with easy onboarding extra layer of security meeting organizational second authentication or MFA, multi-factor authentication, compliance requirements without sacrificing the user experience. MFA near-eliminates the risk of user impersonation or the use of compromised credentials. The adoption of an organizational multi‐factor authentication policy will protect an organization’s servers, systems, software, and members privacy while demonstrating compliance to federal, educational and industry mandates.
- Can be used on several different types of devices, such as iPhones, Android phones, computers, tablets, and even watches thereby achieving MFA, multi-factor authentication, organization-wide and secure access principles (authentication and authorization).
What is an authenticator app?
An authenticator app is a software tool typically downloaded and installed on a smartphone, but can also be installed on a tablet, notebook, desktop, and even several types of smart watches. The authenticator app generates a 6 to 8 digit one-time use security key code that’s valid for a brief window of time and used in conjunction with your usual login credentials to successfully login and access an account.
Hence once you set up an authenticator app with an account, every time you log into that account going forward you first open the authenticator app and submit the security key code presented with your usual credentials. Logging in now involves the server and authenticator app with the server performing a real-time crypto operation. Successful login happens in the blink of an eye and signifies that both the server and the authenticator app have shared and are in agreement on the security key code or ‘2nd factor of authentication’.
Authenticator app security key codes are generated by an algorithm and in our case, the FEITIAN authenticator app uses what’s called a TOTP or Time-Based One Time Password. The length of time in which each generated password is valid is referred to as a timestep. As a rule, timesteps are set to 30 seconds or 60 seconds in length. Thus, if you’ve not used the ‘just generated’ security key code the authenticator app has provided you in conjunction with your usual login credentials within the limited window of time, the security key code will be invalidated. If a timestamp expires the security key code is no longer usable and you’ll need to repeat the process of requesting a security key code to access the account.
Authenticator apps like the FEITIAN’s authenticator app are sometimes referred to as 2FA, two-factor authentication, or MFA, multi-factor authentication tools. This means it takes 2 separate and different security measures for successful verification and access to an online account. For example, when attempting to log in, you’ll need both traditional credentials and the security key code that the authenticator app generates for verification and access to an account. MFA, multi-factor authentication, keeps accounts more secure because the security key code changes every 30 or 60 seconds, thereby making efforts to hack the security key code a futile proposition for online attackers. MFA, multi-factor authentication, is an effective protection against threats like credential stuffing, phishing attacks, and account takeovers.
Companies are using MFA, multi-factor authentication, to ensure no unauthorized party has access to online accounts. While FEITIAN FIDO, Fast Identity Online, security keys (actual physical digital keys, click here) are more secure than using the FEITIAN and any authorization app alone, they’re not for all situations nor always the most convenient. If carrying around and possibly losing a physical digital USB drive sized key is highly probable for you, an authorization app on your phone is better suited for you.
Are authenticator apps accessing data on your phone?
A secure authenticator app might check to understand what operating system (OS) and browser you’re using. Authenticator apps need to confirm functionality with your OS and browser. An out-of-date operating system might introduce security gaps in your device exposing your data to risk.
Thus if an authenticator app instructs you to update your phone or tablet’s operating system or browser, that doesn’t mean the authenticator app has crawled through your entire phone’s private information. This simply means the authenticator app identified a compatibility risk to be addressed, no more, no less. Authenticator apps cannot access your accounts, and once they’ve generated and presented the security key code, they don’t communicate with the site.
Why should I use an authenticator app?
The key reason for implementing an authenticator app is to add a second layer of security to online accounts and protect against identity theft. Thus you should be using an authenticator app to:
- Achieve 2FA, two-factor authentication, a form of MFA or multi-factor authentication, based on an algorithm linked to your phone that’s continually generating fast expiring security key codes. This serves as a second layer of security for your web-based accounts like Salesforce, Facebook, Microsoft, Google, etc.
- Meet compliance obligations & legal requirements for financial, HIPAA / healthcare, education, Government, defense contractors, technology and more business spaces.
- Implement a “zero trust strategy”, which amounts to a ‘never trust and always verify’ approach effectively securing an organization by eliminating implicit trust and continuously validating every stage of digital interaction. Previous security approaches assume users, devices, and infrastructure inside an organization’s network can be trusted, this is no longer the case. A zero trust approach treats every attempt of access as if it’s unauthorized and not to be trusted — so access won’t be permitted until trust is demonstrated via 2FA, or MFA, multi-factor authorization.
- Not have your organization become a statistic. Here are the phishing attacks statistics per April 2023 that you should be aware of. Statistics by Norton indicate 88% of organizations are subject to spear phishing attacks yearly. A 2019 Symantec Threat Report indicated 65% of cyber-attacks are attempted through spear phishing. Phishing breaches took about 10 months to identify & contain, according to IBM’s 2022 Data Breach Report.
- Achieve cloud-based, scalable network security without having to manage security appliances, complex software configurations or expensive support contracts.
Why is an authenticator app safer than an SMS text message?
Security key codes that are delivered to phones via SMS text messages are vulnerable to hackers in multiple ways such as:
- SIM swapping
Using only the last 4 digits of your social security number, hackers are effective in redirecting phone numbers with phone carriers to a new device – from which they can retrieve all your text messages. - Forged authorizations
Hackers routinely forge an authorization through a third party company that provides rerouting services. This hack is popularly aimed at businesses because the hacker can have multiple numbers rerouted to other phones in one fell swoop, including computers. - Listening in
By using what’s called an SS7 attack, hackers spy directly on phone carrier networks, intercepting text messages. - Hacking phones directly
Hackers can intercept everything that happens on a phone if they can hack through phishing emails. Also, when a business’s servers or network are hacked, connected devices are at risk of being compromised. - Since SMS text authentication is usually valid for 5, 10, 30 minutes and more, hackers with user’s accompanying credentials are in hand have plenty of time to use the SMS text message delivered security key code to their advantage.
Authenticator apps have several variants to secure the environment. FEITIAN’s model follows OATH TOTP protocol and cryptographically generates a one-time passcodes to be used as MFA. Other variants may use push notification for users to tap and confirm.. Other variants use contextual information to validate and make sure that the app is not in the hacker’s hands or being phished
An authentication app is linked directly to the physical phone device. Since the security key codes are not delivered over the phone carrier network, hackers are not able to intercept the security key codes through SMS text message hacks. Hence even if hackers were to reroute your phone number, or hack into your phone carrier’s network, they still wouldn’t receive the security key codes.
Authenticator apps cannot access your accounts and once they’ve generated and presented the security key code, their job is done and they cannot communicate with the site you’ve logged onto. Security key codes provided through your authentication app work one time and expire in 30-60 seconds swiftly eliminating unauthorized exposure to your protected servers and systems.
How to set up your online accounts
Authentication apps mostly follow a similar basic protocol when you’re adding a new online account. For many accounts you only need to scan a QR code affiliated with your account, and once it’s done, everything is saved in the app. However, there are also manual set up protocols. To set up 2FA, two-factor authentication, also known as MFA or multi factor authentication by authentication app instead of text message, go to your chosen site’s security settings and you’ll likely see a two-factor or multi factor authentication section. Most sites list the SMS text message code options first, but usually somewhere near you’ll see authenticator app support. For example, with Facebook:
When activating two-factor authentication, you can choose for your primary security method to be a third-party authentication app.
Use a third-party authentication app for login codes
- Install a third-party authentication app on your device. It’s best to install the app on the device you normally use to access Facebook.
- Go to your Security and Login Settings.
- Scroll down to Use two-factor authentication and click Edit. You may be asked to re-enter your password at this point.
- Click Use Authentication App when you’re asked to choose your security method.
- Follow the on-screen instructions.
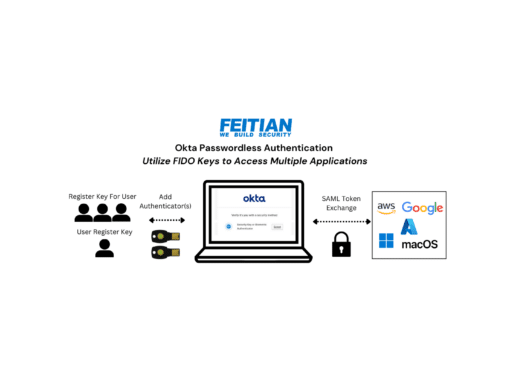
adding a hardware authentication device (physical key)
Since the protocol used by MFA, multi-factor authentication, products is usually based on the same standard, businesses routinely mix and match brands, for instance, using FEITIAN Authenticator to get into your Microsoft Account or Google Account.
While the most commonly used MFA, multi-factor authentication, is a one-time-use security code texted to your phone, the most secure version deploys an authenticator app coupled with a physical security key device instead of a phone. With an actual physical security key device, nobody can get into the accounts where you set it up unless they have both your password and physical access to the key device. FEITIAN has physical security keys designed for use with Android phones, Apple phones, and even passworldless fingerprint biometric keys and more.
Physical security keys about the size of a USB drive are single-purpose, security-hardened devices, giving them a distinct advantage over solely using an authenticator app. Though rare, it’s not impossible to have a malware-infested app running on your phone from a successful phishing email and thereby have the security codes produced by a phone’s authenticator app intercepted. A physical security key’s entire functioning is an isolated siloed event within the device itself. FEITIANhas everything from security keys for use with mobile devices to passwordless fingerprint biometric keys and more.