In today’s digital age, cybersecurity threats continue to evolve, making traditional password-based authentication methods increasingly vulnerable. To address this challenge, enterprises are embracing passwordless authentication solutions to bolster security and enhance user experience.
Our latest case study delves into the transformative journey of a leading enterprise that leveraged passwordless authentication to safeguard its sensitive data and streamline authentication processes.
Let’s take a closer look at a few key highlights:
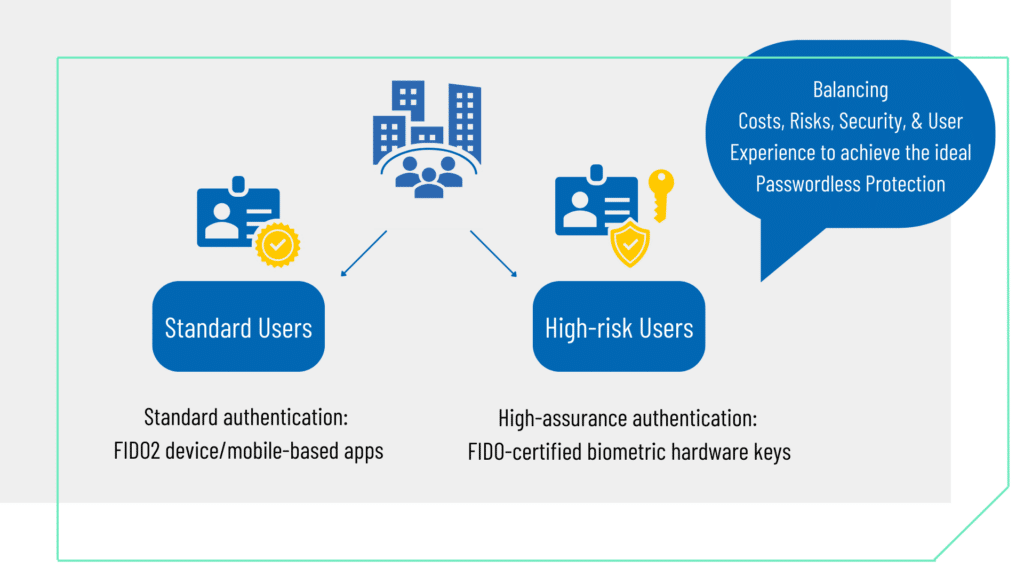
- FIDO2: The Game Changer: After careful consideration, the enterprise opted for FIDO2 as a standard to authenticate to applications and online services, on both mobile and desktop environments, using unique cryptographic login credentials. They selected FEITIAN’s FIDO2 security keys to further enable their passwordless journey. With a focus on user experience and security, the enterprise selected FIDO2 keys from FEITIAN for both standard and high-assurance users.
- Why FEITIAN?: FEITIAN emerged as the preferred vendor, offering a wide range of FIDO-certified keys with robust security features and compatibility across various devices. The enterprise benefited from streamlined purchasing, positive customer references, and cost-effective pricing.
Ready to learn more? Dive deeper into this compelling case study to uncover valuable insights and best practices for implementing passwordless authentication in your organization. Download the full case study today and unlock the potential of passwordless authentication for your enterprise.
Join us on the journey towards a more secure and seamless authentication experience. Together, let’s empower enterprises to embrace the future of authentication with confidence and resilience.
WHAT’S NEXT?
FEITIAN Technologies provides innovative products, ranging from multifactor authentication to secure hardware tokens, empower organizations to safeguard their digital assets effectively. By integrating FEITIAN’s state-of-the-art security solutions into your cybersecurity strategy, you can significantly reduce the risk of falling victim to devastating attacks.
Interested in speaking with a specialist? Click here
Check out these other relevant articles: