You may be rubbing your eyes wondering if you are reading an old, outdated blog post, but fortunately (or unfortunately) this is a current article and it is still the year 2021. t is how dire the need is to protect ourselves with MFA (Multi-Factor Authentication). Every day, we hear about hacking incidents, account takeovers, and ransomware attacks that not only threatens business sectors, but potentially people’s health as well.
Now that the U.S White House is driving the importance of cybersecurity into the mind of businesses and IT leadership, starting with executive order 14028, which pushes federal agencies to adopt zero-trust infrastructure, proper MFA, and FIDO security with derived PIV credentials, there is no doubt that individuals and businesses need to adopt the proper MFA today.
While the latest and the greatest FIDO solution is unquestionably the most secure, we want to remind everyone that despite being 15-20 years old, OTP tokens are still a great option for MFA and 2FA, especially for medium to large organizations.
Compared to other alternative MFA options, OTP tokens have a few differentiators to consider.
- Works completely offline and does not require being plugged into any systems (unlike security keys).
- Better controlled for large, regulated companies where cryptographic seeds are centrally managed.
- More budget friendly.
We’ve recently wrapped up a successful technical webinar on OTP authentications and could re-work some of the content to help understand how OTP works and why we consider it still a great MFA option.
Authentication typically works with a few factors:
- Something you know: Password, security questions, PINs
- Something you have: Things in the users’ possession, e.g., smartphones, hardware tokens
- Something you are: Usually biometric factors (Fingerprint, iris, Face ID, etc)
FIDO security keys and OTP tokens establish ‘something you have’, while the biometric FIDO keys can help securely establishing ‘something you have’ AND ‘something you are’.
The way OTP can securely establish the ‘something you have’ factor, is by using a symmetric shared secret and the magic of HMAC cryptographic function.
Here are a few variances of OATH OTP standards:
- HOTP: HMAC-based OTP = Event based
- TOTP: Time-based OTP (also using HMAC) = Time based
- Challenge-Response: another extension but less common nowadays.
As shown in the graphic below, the shared secret (aka the ‘seed’), is combined with the variable (for HOTP, it’s a counter; for TOTP, it’s the time) to process through a cryptographic function to deduce the OTP code you get from the OTP tokens.
When an OTP token is purchased, it will come with a pre-programmed ‘seed’. The seed file is then uploaded to the IdP, which is then activated and assigned to a user. During the authentication time, both the IdP server, and the OTP token (when pressing the button) will run through the calculation above, to generate the code. Subsequently, the user enters the code, the server checks to see if that matches it’s own calculated code and will verify the identity of the user.
Since different IdP may require different seed value encoding (some may require different HMAC hashing function at SHA256 as to the default SHA1), it will help simplify the deployment by identifying and communicating these requirements. FEITIAN provides many formats, but 3 of the most popular are the following: (please add a note at the time of ordering to let us know the format you required!)
- Hexadecimal (most common)
- Base32 (Azure Active Directory entails this)
- PSKC(RFC6030) xml
Seed programming
If you want to ensure full control on your organization’s OTP seed secrets, you might want to consider looking into FEITIAN’s OTP programming offering. We provide different options for programming OTP tokens, as well as OTP features embedded inside our FIDO security keys.
To better understand, here is a video on FEITIAN’s OPT Self Programming Solution
Just like any other technology, OTP authentication also has its weaknesses. As the secret is ‘shared’, seed file management becomes the critical factor. If the seed data gets into the wrong hands, it could cause some havoc.
As mentioned earlier, OTP authentication has been aging well and is still proving to be a strong option for your organization’s MFA needs.
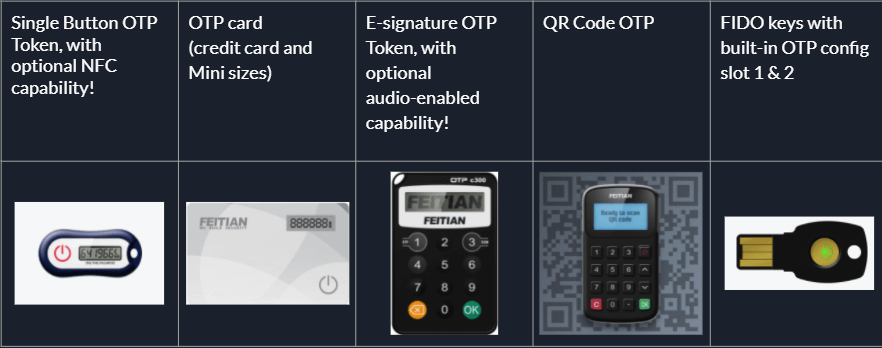
Here is FEITAIN’s OTP token portfolio.
Looking to deploy OTP?
Contact our security experts to learn about FEITIAN’s OTP products and solutions and how we can get you on the path to stronger authentication.
[super_form id=”5652″]