Event/Time-Based OTP Token
FEITIAN Event/Time-Based OTP Token
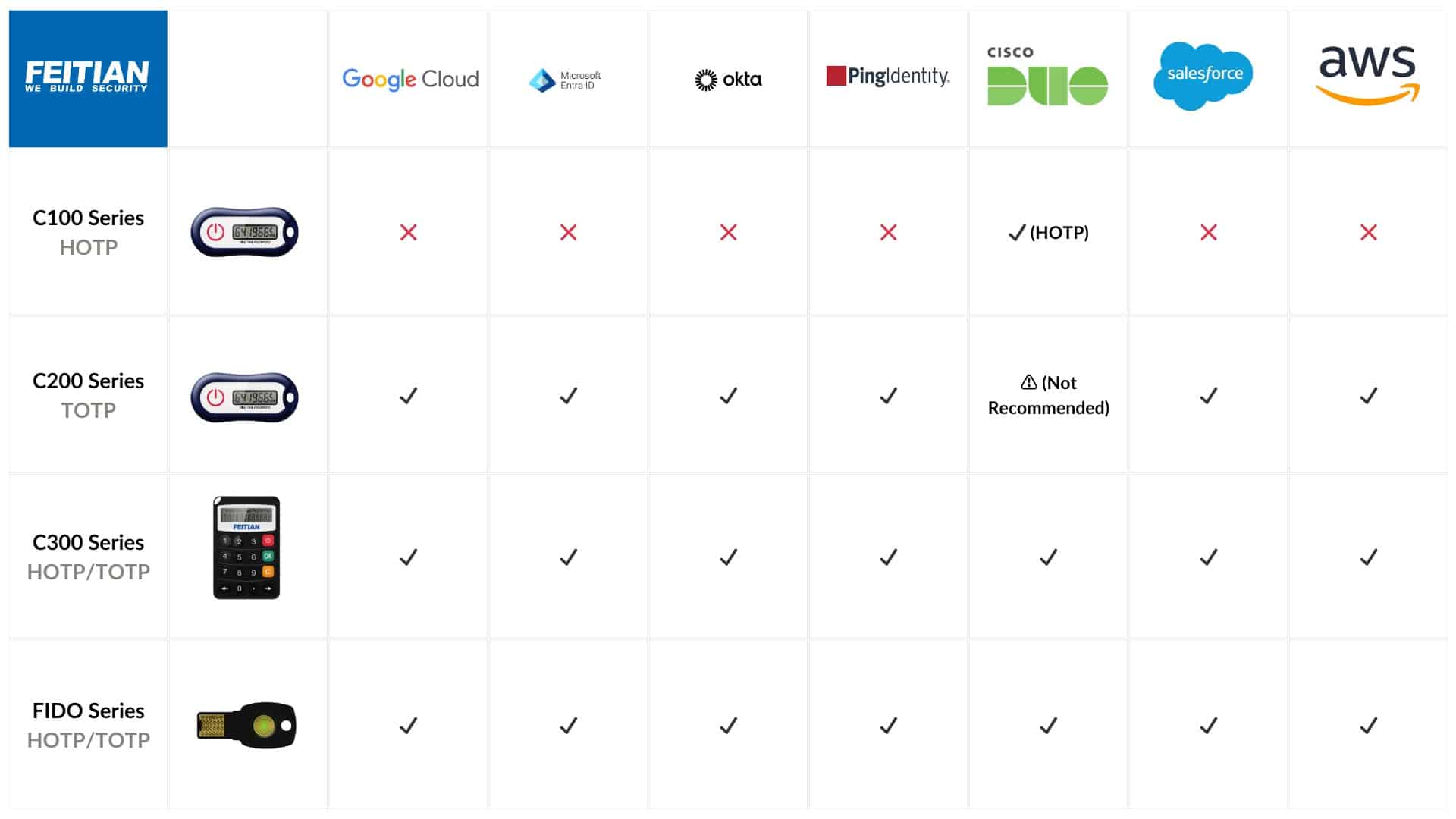
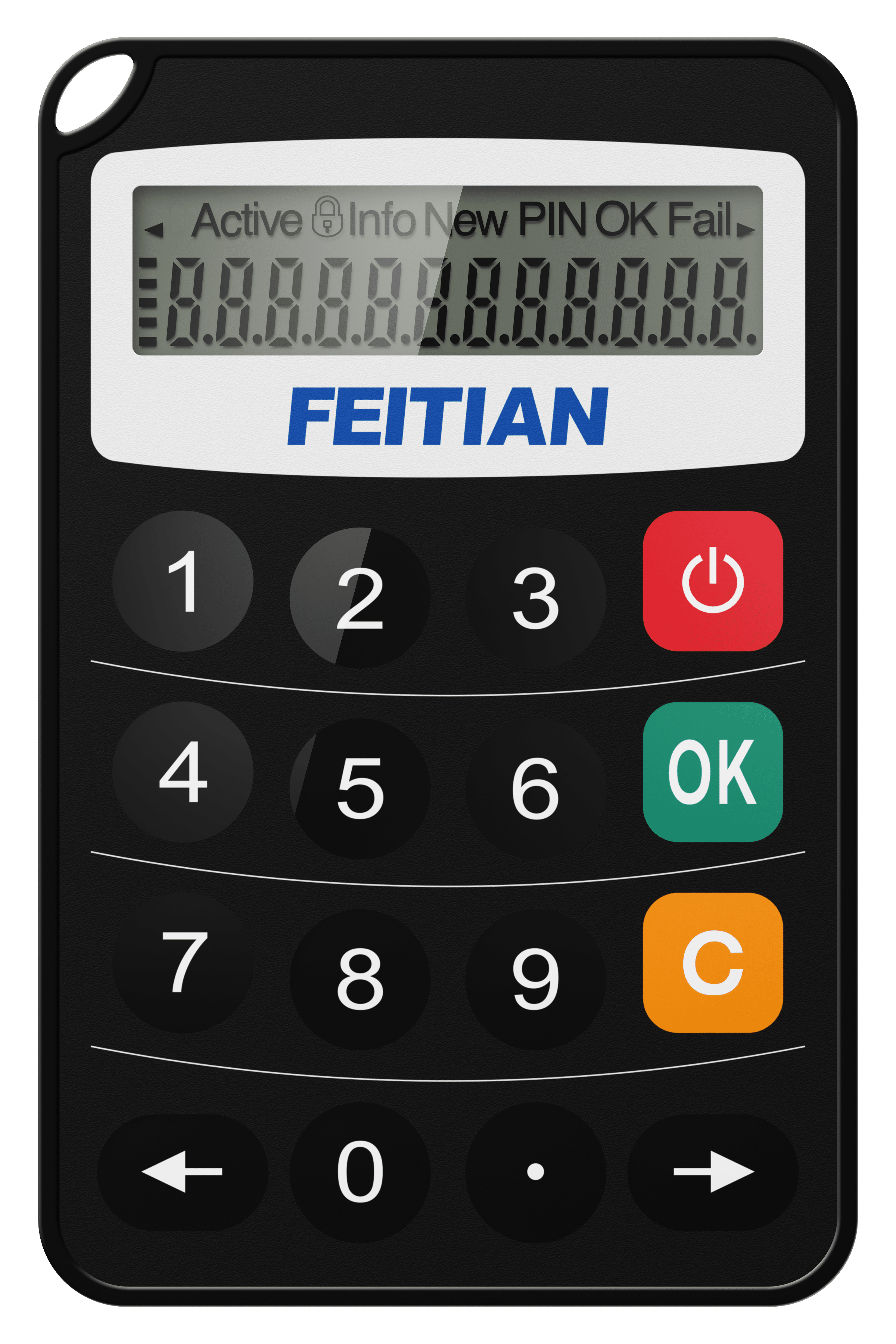
The OTP c300 hardware token provides OATH event/time-based and challenge response one-time-password. The OTP c300 effectively eliminates many threats by secure your accounts with a second factor authentication.
Key Verification Method: Passcode
Application: 2FA
Interface Type: Event/Time Display
$20.25
More Details About Product
Two-Factor Authentication (2FA): OTP tokens are commonly used for two-factor authentication, where users combine their regular username and password with a one-time password generated by the token. This adds an extra layer of security to access systems, applications, or online platforms, reducing the risk of unauthorized access.
Remote Access and VPN: OTP tokens are used to establish secure remote access and Virtual Private Network (VPN) connections. Users generate a unique OTP from the token and provide it during the authentication process to gain secure access to remote servers or corporate networks. This ensures that only authorized individuals can establish a connection and protect sensitive data.
Online Banking and Financial Transactions: OTP tokens provide an additional security measure for online banking and financial transactions. Users generate a one-time password from the token and input it along with their regular login credentials to authenticate their identity during financial transactions, such as making payments, transferring funds, or approving transactions. This helps protect against unauthorized access and fraudulent activities.
Identity and Access Management (IAM): OTP tokens are widely used in Identity and Access Management systems to enhance security. Users generate one-time passwords from the token to verify their identity when requesting access to specific resources, applications, or privileged accounts. This ensures that only authorized individuals can access sensitive information and resources.
Secure Document Signing: OTP tokens can be used for secure document signing. Users generate a unique one-time password from the token and use it as a digital signature to authenticate and validate electronic documents. This adds an extra layer of security and integrity to important documents, contracts, or agreements.
Physical Access Control: OTP tokens can be used for physical access control systems. Users generate a one-time password from the token and input it into access control devices to grant or deny access to specific areas or buildings. This helps ensure that only authorized individuals with the correct OTP can enter restricted areas.
Secure Email and Messaging: OTP tokens can be integrated into secure email and messaging systems. Users generate one-time passwords from the token to authenticate their identity when sending or accessing sensitive emails or messages. This ensures that communication remains confidential and protected from unauthorized access.
Password Reset and Account Recovery: OTP tokens can be used for secure password reset and account recovery processes. Users generate a one-time password from the token and use it as an additional verification factor when resetting passwords or recovering locked accounts. This adds an extra layer of security to account management processes.
VPN Token: OTP tokens can be dedicated VPN tokens, where the generated one-time passwords are specifically used for VPN connections. Users input the OTP along with their login credentials to establish secure VPN connections, protecting sensitive data during remote access.
Physical Asset Protection: OTP tokens can be used to secure physical assets, such as safes, lockers, or storage units. Users generate a one-time password from the token and input it into the corresponding access control system to unlock or gain access to the protected asset. This helps prevent unauthorized access and ensures the security of valuable items.
Product Features:
FEITIAN Event/Time-Based OTP Token Downloads
Product reviews
Other Suggested products
OTP OATH Event-Based Display Card (HOTP) (VC-100E)

OTP OATH Time-Based Display Card (TOTP) (VC-200E)
Questions? Contact Sales
"*" indicates required fields



Reviews